LAC Co., Ltd. is a leading cybersecurity and system integration company in Japan, renowned for launching the country’s first security services in 1995. With deep expertise in vulnerability diagnostics, threat analysis, and managed security services, LAC supports thousands of enterprises and government agencies in building resilient digital infrastructures. As a member of the KDDI Group, LAC benefits from strong technological synergy and expanded capabilities, enabling it to deliver comprehensive, cutting-edge solutions that address today’s evolving cyber threats.
Cybersecurity World Asia 2025 - LAC


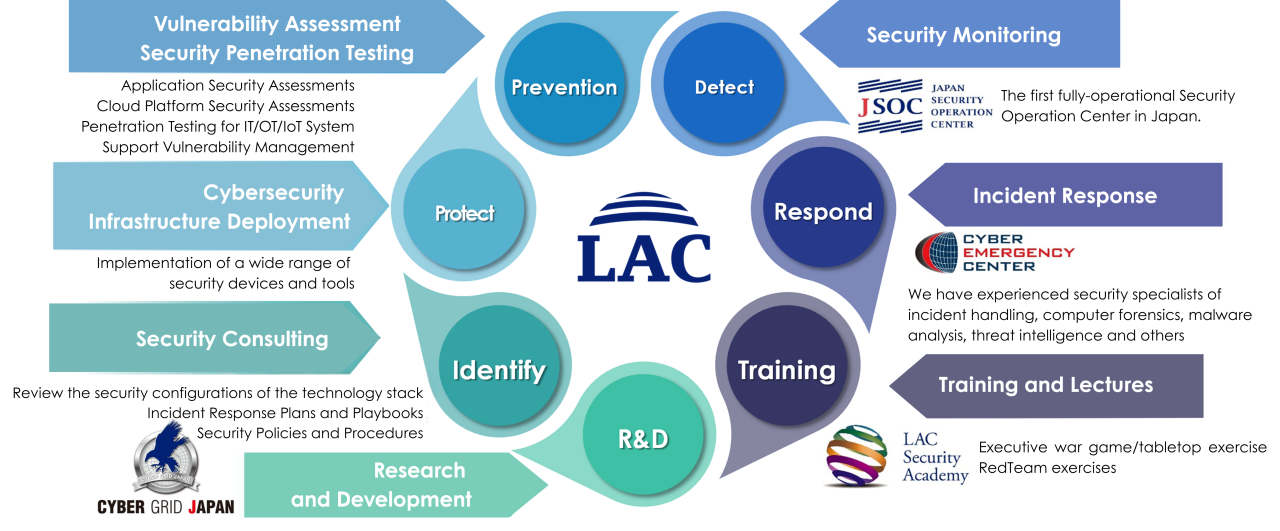
Services and Solutions
1. Assessment - Risk Assessment Service
Understand fully your currrent overall cyber security capabilities against the latest threats and enhance your efficiency!
Let our LAC professional cybersecurity consultants indentify potential risks and advise on the countermeasures for these risks.
With approximately 80 assessment items developed by LAC, we asses current status of cybersecurity posture and evaluate based on a maturity model by the Cybersecurity Maturity Model Certification (CMMC).
- Security Governance
- Service Management
- Facility Management
- Network Security
- Infrastructure Security
- Identity Management
2. Cybersecurity Professional Training
Time is precious — and while your schedule may be packed, your growth doesn’t have to wait.
If you're eager to enhance your capabilities but can’t spare time for formal training sessions, you're not alone.
Want to learn at your own pace and ensure you truly understand what you've learned?
Practical exercises and hands-on application can bridge that gap — helping you turn knowledge into confidence.
Let LAC security play a part in growing and educating your employees.
- Variety of courses available for general staffs, IT engineers to Cyber Security Expert.
- Online (self pace learning) and In-class seminar
- Online hands-on environment for exercise


3. Automated Penetration - Breach and Attack Simulation (BAS)
Is your security infrastructure truly delivering maximum effectiveness?
Can it detect and stop the latest malware — even threats that emerged just yesterday?
And when the CIO asks, can you confidently demonstrate that your organization’s defenses are up to the task?
Breach and Attack Simulation (BAS) empowers you to:
Launch automated simulations using the latest real-world threats
Rapidly uncover security gaps across your environment
Receive clear, actionable mitigation guidance to strengthen your defenses

Why BAS?

4. Security Monitoring - JSOC
JSOC MSS Lite for Global business - 24/7 Managed Security Service
- Full Operation, Maintenance and Management of an extensive array of network security monitoring devices (F/W, IDS, IPS)
- Proficient policy tuning by maximizing capacity for intrusion detection, intrusion prevention and log analysis systems that can be critical to identifying trouble areas and potential security breaches.
- 24/7 Real time analysis
- 15 minutes Notification and Protection against Critical Incidents (Guaranteed in the SLA)

5. Incident Response Service
Encountered suspicious activity but unsure if it qualifies as a confirmed incident?
Or perhaps you've confirmed an incident — but lack the deep technical expertise to investigate further?
These are common challenges in modern security operations. Without the right tools or expertise, threats can go undetected or unresolved, increasing risk exposure.
LAC supports your entire incident response journey — from detection to mitigation.
Whether you're facing suspicious activity or a confirmed breach, LAC enables:
- Rapid response to suspicious events, minimizing potential impact
- Full-spectrum incident response, including in-depth forensic analysis
- Expert guidance to close gaps and prevent recurrence
With LAC, you’re not just reacting — you’re responding with confidence and clarity.
Related Resources








What is the best solution for your problem?
Please consult a KDDI consultant.


















